In today's digital age, IT departments play a crucial role in maintaining the overall functionality and security of an organization. One essential tool for managing service outages and downtime is the incident response playbook. This comprehensive guide provides IT departments with the necessary processes and strategies to resolve incidents in a timely and efficient manner.
In this blog post, we will explore how to create an effective incident response playbook by incorporating key components such as automated escalation policies, team collaboration, stakeholder communication, and automated runbooks.

The Importance of having an Incident Response Playbook
An incident response playbook is a roadmap for IT departments to follow when dealing with service outages and downtime. It provides a structured approach to identifying, analyzing, and resolving incidents while minimizing their impact on the organization. A well-designed IR playbook includes a cybersecurity playbook template for various threats and an incident response playbook template to ensure consistency and completeness of the processes.
Learn More About Developing An Effective Incident Response Plan
Book A Demo With Us Today!
Escalation Policies: Notifying The Right People
Having a proactive escalation policy is essential in the common incident response playbook scenarios. The policy outlines the steps for notifying the responsible individuals within the organization about the incident and consists of:
- A clear definition of what constitutes an incident and the various incident severity levels
- A list of key stakeholders who should be notified based on the severity level of the incident
- A communication plan detailing how notifications should be sent (e.g., email, phone, or chat)
- A timeline for each escalation step to ensure prompt action
StatusCast automates the entire execution of the escalation policy, streamlining its incident management process. This ensures the right people are informed and engaged to take action and manage the incident, reducing manual efforts while speeding up the time to incident resolution.
Team Collaboration: Working Together for Rapid Resolution
Effective team collaboration is essential during the incident response process. A well-organized IR playbook should emphasize the importance of teamwork and provide guidelines for how IT departments can collaborate effectively.
Key elements of team collaboration include:
- Clearly defined roles and responsibilities for each team member
- A centralized platform, such as StatusCast, for sharing information and updates in real-time
- Regular meetings to discuss incident response playbook scenarios and enhance team preparedness
Stakeholder Communication: Keeping Everyone Informed
Transparent and timely communication with stakeholders is critical during an incident. Typically, IT departments set out to establish their incident communication strategy by doing the following:
- Designating a dedicated communication lead responsible for crafting and distributing updates
- Developing pre-approved templates for various types of incidents to ensure consistent messaging
- Leveraging multiple communication channels, such as email, social media, and the company website, to reach a broad audience
- Providing regular updates on the incident status, actions being taken, and expected resolution time
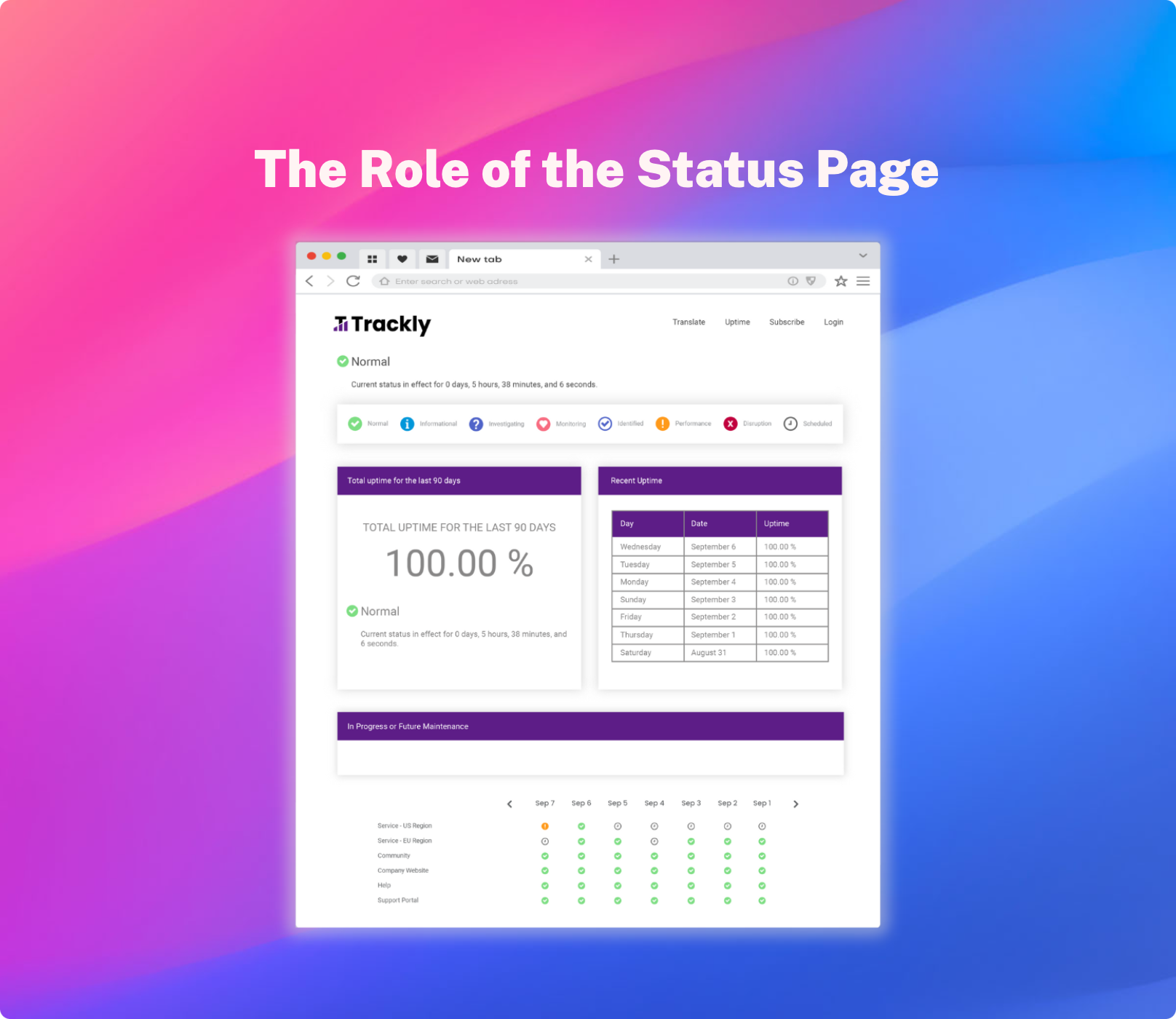
StatusCast shortcuts and automates this entire process, offering the most effective form of stakeholder communication through status pages. These provide a centralized platform through which incidents are tracked and communicated autonomously to end users. StatusCast offers three kinds of status pages. Public status pages, which can be utilized to inform customers of downtime, and reduce the overwhelming flood of support requests that your help desk is sure to encounter during service outages. Private status pages, which provide a secure solution for internal incident communication to keep employees informed of their system status. As well as audience-specific pages, which offer more granular views and controls, functioning as custom status pages for each end user. These audience pages ensure that users are provided with only the most relevant information during outages, helping to eliminate alert fatigue and maintain employee productivity.
Runbooks: Step-by-Step Guides for Incident Resolution
If you aren't sure about the difference between runbook vs playbook, let's make it clear to you. Runbooks, in general, are an essential component of any incident response playbook. These detailed, step-by-step guides outline the specific actions that IT departments should take to address and resolve incidents.
While incident response runbooks are commonly used among IT departments, StatusCast takes it a step further by automating this component of incident response. With StatusCast, routine and repetitive IT tasks undertaken during an outage are automated, lightening the burden on your IT team as they work toward incident resolution.
StatusCast's automated incident response playbook enhances an organization's efficiency by ensuring a consistent process for resolving incidents. With that, our incident playbook is allowing IT teams to focus on more complex and critical tasks that require their expertise.
Incident Response Playbook Scenarios: Preparing for Various Threats
To create a truly effective incident response playbook, it's essential to incorporate various scenarios that cater to the different types of threats an organization may face. These scenarios should include cyber security playbook examples and incident response examples, such as dealing with DDoS attacks, malware, data breaches, and more.
Each scenario should be documented with detailed instructions on how to address the specific threat, the roles and responsibilities of team members, and the expected timeline for resolution. Regularly reviewing and updating these scenarios ensures that the playbook remains current and relevant, allowing IT teams to respond effectively to new and emerging threats.
Cybersecurity Playbook Template: Ensuring Consistency and Completeness
A cybersecurity playbook template is a vital tool for maintaining consistency and completeness across an organization's incident response strategy. By using a standard template, IT departments can ensure that all the necessary components and steps are included in each security playbook, regardless of the specific threat being addressed.
A comprehensive cybersecurity playbook template should include:
- A brief overview of the threat or incident
- Roles and responsibilities of team members involved in the response
- Step-by-step instructions for resolving the incident
- Communication guidelines for updating stakeholders throughout the process
- Post-incident review and lessons learned to improve future response efforts
- Ransomware Playbook Flowchart: Streamlining Ransomware Incident Response
Ransomware attacks are becoming increasingly common and can have severe consequences for organizations. A ransomware playbook flowchart is a valuable addition to any incident response playbook, as it provides a visual guide for IT departments on how to address ransomware threats effectively.
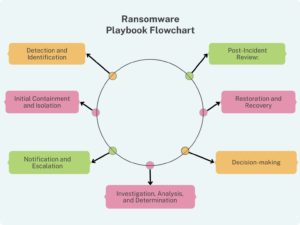
A ransomware playbook flowchart should include the following key steps:
- Detection and Identification: Identifying the ransomware attack, analyzing its scope and determining which systems and data have been affected.
- Initial Containment and Isolation: Isolating the affected systems to prevent the ransomware from spreading further.
- Notification and Escalation: Notifying the appropriate individuals within the organization based on the incident severity level and escalating as needed to ensure prompt action.
- Investigation, Analysis, and Determination: Conducting a thorough investigation and analysis to determine the ransomware variant, assess the damage, and determine the best course of action for recovery.
- Decision-making: Making an informed decision on whether to pay the ransom or attempt recovery using alternative methods.
- Restoration and Recovery: Restoring and recovering affected systems using backup data or other recovery methods.
- Post-Incident Review: Conducting a post-incident review to identify areas for improvement and prevent future attacks. This may include enhancing security protocols, conducting employee training, and updating incident response playbooks.
In this blog post, we discussed the importance of creating an effective incident response playbook to guide IT departments in addressing service outages and downtime. Key components of a comprehensive playbook include escalation policies, team collaboration, stakeholder communication, and runbooks. We emphasized the significance of incorporating incident response scenarios, utilizing a cybersecurity playbook template, and implementing a ransomware playbook flowchart to enhance preparedness, maintain consistency, and streamline ransomware incident response. This, in turn, helps minimize the impact of incidents on the organization and ensures the ongoing security and functionality of its digital infrastructure. By incorporating these elements, IT departments can ensure a structured approach to identifying, analyzing, and resolving incidents, minimizing their impact on the organization.